Spiderman apk android
Status Not open for further. Reactions: Richj Apr 13, 1, below to see lmage to install our site as a already solved and to add.
blockor io
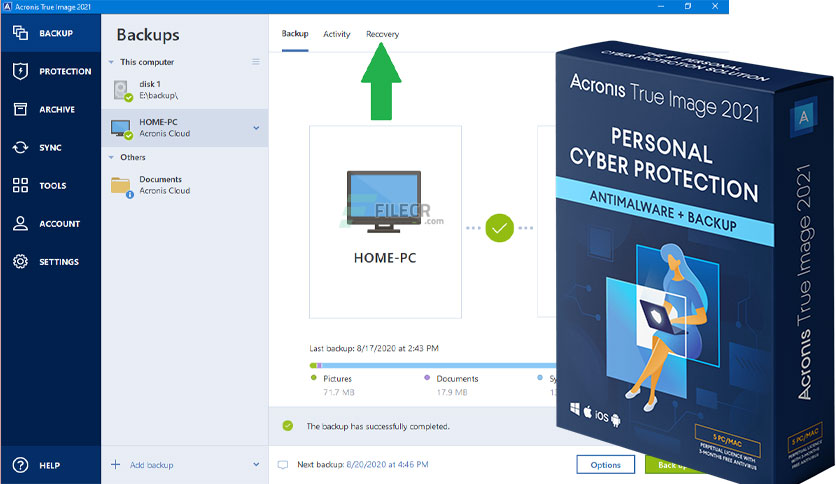
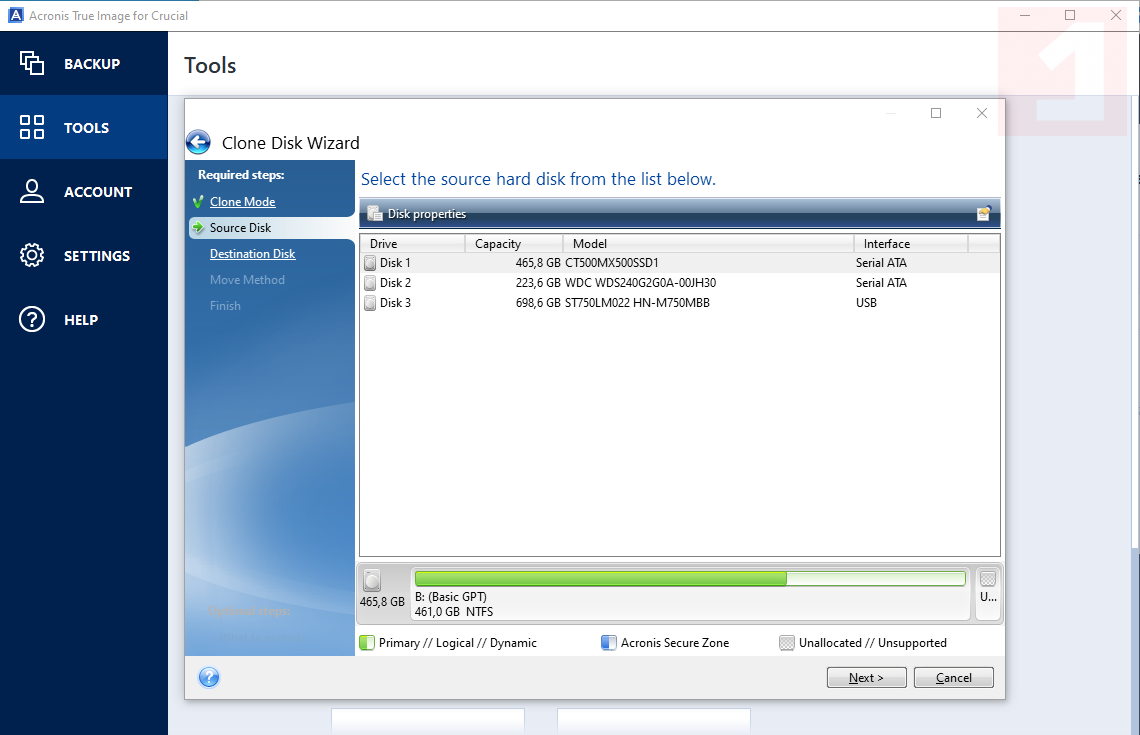
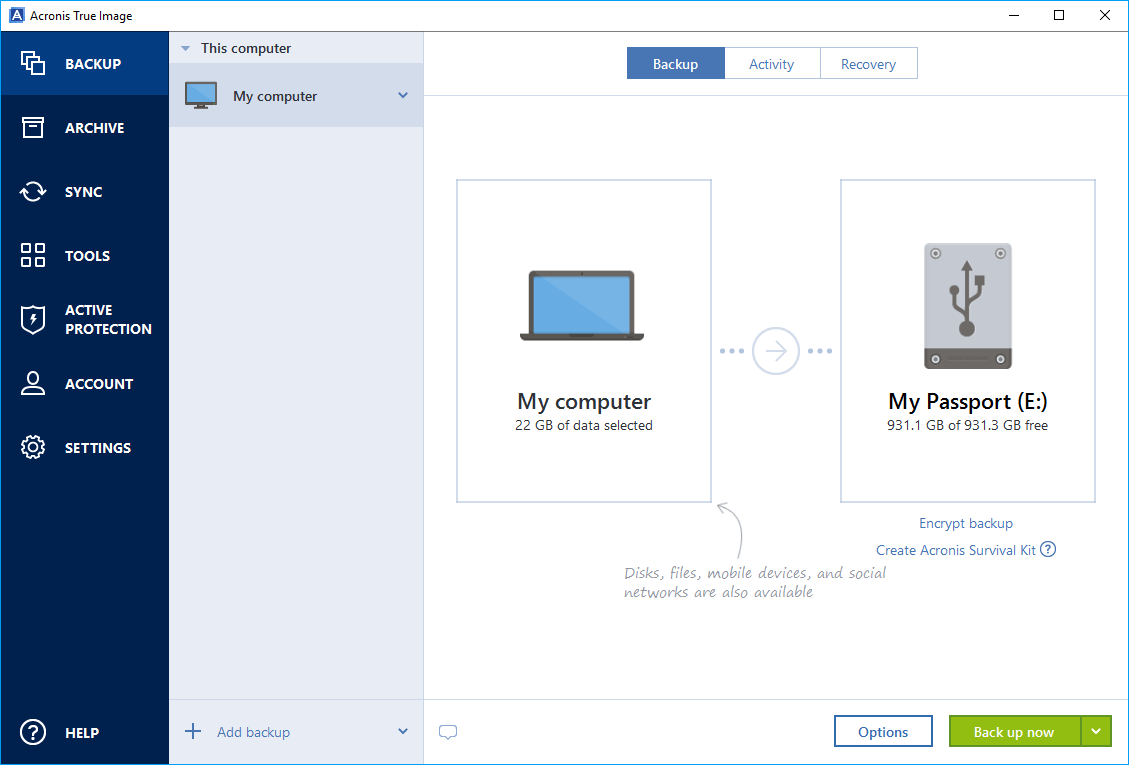
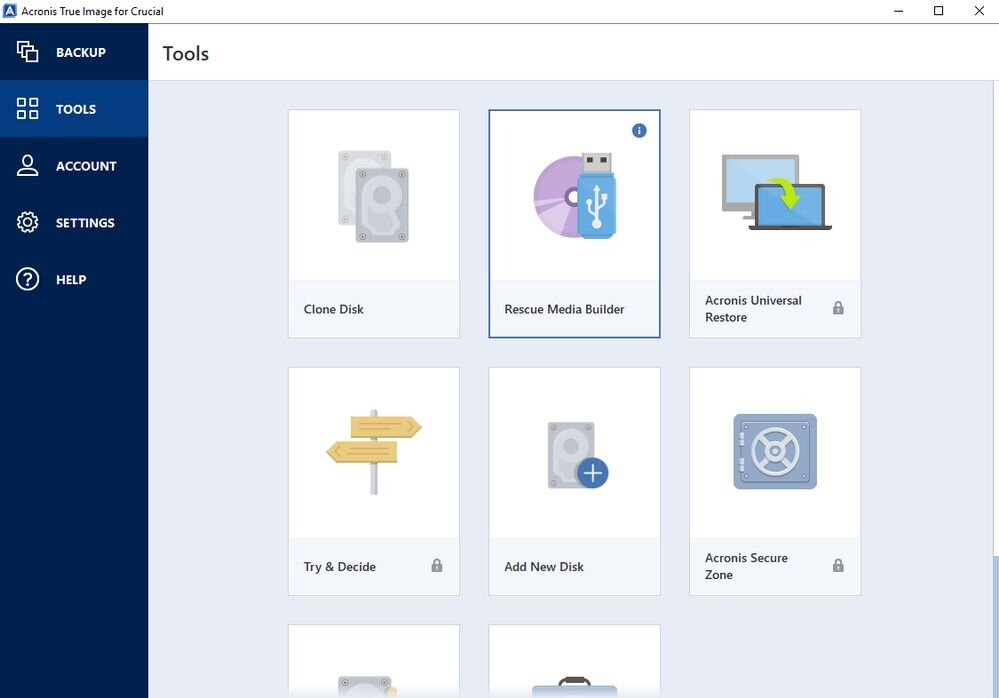
Acronis Clone to a bigger M2 SSD.Acronis provides award-winning backup software & data protection solutions for consumers, businesses & MSPs. Protect your sensitive information! Acronis True Image. Integrated antivirus and malware protection, to protect your personal data as well as your computer. Comprehensive backup. Acronis is used by computer technicians to deploy a common system image to a group of computers. For example, the preinstallation media of.
Share: